Security vs. Compliance: What’s the Difference?
Businesses across industries and continents are now obligated to satisfy various compliance standards, from GDPR to CCPA. But, how do you actually ensure compliance? By securing the information your organization handles.
This – of course – is easier said than done and requires cross-team collaboration. In this article, we’ll explain:
- What Information Security means
- What compliance means
- How these concepts differ
- Why you can’t neglect one in favor of the other
Looking for more information about specific data privacy laws? Visit our compliance content hub.
Security and Compliance: The Difference
“Security” is the infrastructure, tools, and policies you put in place to protect your company’s information and equipment.
“Compliance” is the act of meeting a required set of security and regulatory standards.
As you might have guessed, security and compliance are very closely linked, and each should drive the other. Keep reading to learn more about the key concepts you need to consider to ensure your organization’s information systems are up to scratch.
Security: Key Concepts
When it comes to information security, organizations have to safeguard every vector that stores and transfers data. In this article, we’ll cover network, device, and employee security.
Network Security
While every organization is different, most IT leaders are concerned with protecting network security. Why? Because employees access company data via various networks, including:
- Your company’s own network — which can be as secure as you are prepared to make it.
- Your employees’ home networks — which you can’t assume will be secure.
- Public networks — such as on public transport and in coffee shops, which are notoriously not secure.
Importantly, data can be intercepted or exfiltrated across all of the above networks. But, there are several steps you can take to mitigate network security threats:
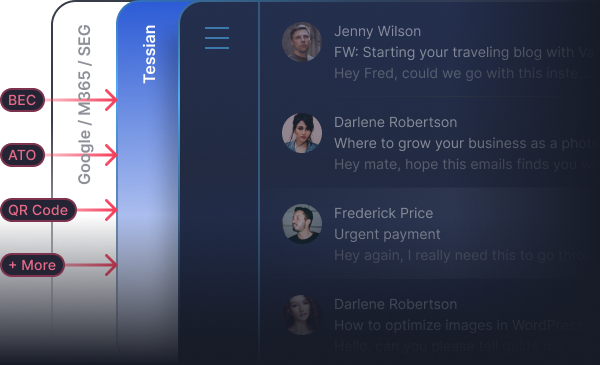
- Email security software — Email security software is a critical requirement in most compliance regimes and should protect against both inbound threats like spear phishing and outbound threats like misdirected emails. Check out this blog to learn How to Choose the Right Email Security Software.
- A firewall — Firewalls can be either hardware or software-based. Certain regulations, such as PCI DSS, require both hardware and software firewalls to be in place.
- Access controls — Access controls allow you to restrict network access only to authorized actors. Generally applicable laws, such as the EU GDPR, treat access control as a basic tenet of reasonable security.
Looking for advice on how to secure data while employees are working remotely? Check out this article: Ultimate Guide to Staying Secure While Working Remotely.
Device Security
Your organization is responsible for devices that store and handle vast amounts of data, including the personal information of your customers and the confidential information of your company.
This applies to any devices that process company data — whether they belong to your company or your employees — including:
- Desktop computers
- Laptops
- Mobile phones
- Tablets
- USB storage devices
You can protect these devices in multiple ways, including:
- Antivirus software
- Multi-factor authentication (MFA)
- Device encryption
- Endpoint security
- Anti-theft tools
Employee Security
88% of data breaches are caused by human error. That’s why employee training is an essential component of any security strategy and a requirement under compliance standards.
A security training program should teach employees:
- How to identify and respond to threats such as phishing, smishing, and vishing
- Why security policies exist and how to follow them
- How to safely handle and dispose of data
You can learn more about the pros (and cons) of security training in this article: Pros and Cons of Phishing Awareness Training.
Compliance: Types of Standards
There are several types of laws, regulations, and certifications that businesses must comply with and they all outline minimum security standards.
So, what happens if your security measures don’t comply with relevant standards?
Your organizations will either be in breach of the law, in danger of being reprimanded by your industry’s regulator (which could include a hefty fine), or unable to obtain or maintain a particular certification.
Generally-Applicable Laws
Some laws apply to every business operating in a given jurisdiction, regardless of sector. Compliance with these laws generally requires the implementation of “reasonable” security measures specific to their industry and proportionate to their size.
Let’s look at two examples.
General Data Protection Regulation (GDPR)
The EU General Data Protection Regulation (GDPR) applies to every person and organization operating in the EU or targeting EU residents. It sets down minimum requirements for information security and privacy.
In particular, covered organizations must:
- Analyze and mitigate security risks
- Encrypt, pseudonymize, or anonymize personal information as appropriate
- Control access to premises, equipment, and digitized personal information
You can learn more about the GDPR in this blog: GDPR: 13 Most Asked Questions + Answers
The GDPR offers some flexibility, accounting for the current state of technology, and the costs involved in securing personal information. However, all organizations must implement “appropriate technical and organizational measures.”
California Consumer Privacy Act (CCPA)
The California Consumer Privacy Act (CCPA) applies to certain businesses that collect California residents’ personal information. It requires that businesses take “reasonable security measures” to secure personal information in their control.
For CCPA-covered businesses, implementing a minimum reasonable security level means complying with the 20 Critical Security Controls from the Center for Internet Security (CIS). The controls include:
- Email and web browser protection
- Account monitoring and controls
- Penetration testing
A business’s security measures may be “appropriate to the nature of the information” that business controls — so highly sensitive personal information will require stronger security measures to protect it.
You can learn more about the CCPA in this blog: CCPA FAQs: Your Guide to California’s New Privacy Law.
Sector-Specific Regulations
Certain industries handle particularly sensitive information, and there are rules that govern how they protect and store that data.
Health Insurance Portability and Accountability Act (HIPAA)
The US Health Insurance Portability and Accountability Act (HIPAA) applies to healthcare providers and businesses that handle protected health information (PHI).
The HIPAA “security rule” requires covered entities to implement administrative, technical, and physical safeguards over the PHI they control, including:
- Ensuring PHI remains confidential
- Identifying and protecting against “reasonably anticipated threats”
- Ensuring all employees comply with HIPAA
Organizations may vary in the extent to which they implement such security measures, accounting for:
- The size, complexity, and capabilities of the organization
- Its technical, hardware, and software infrastructure
- The costs of implementing security measures
- The likelihood and potential impact of risks to PHI
Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) regulates how organizations handle credit and debit card data. Among other measures, PCI DSS requires organizations to:
- Maintain secure networks
- Encrypt cardholder data
- Regularly review security measures
The number of annual transactions a card handler processes dictates the level of security measures they must implement.
- Level 1 — Over 6 million transactions per year
- Level 2 — 1-6 million transactions per year
- Level 3 — 20,000-1 million transactions per year
- Level 4 — Under 20,000 transactions per year
Certification Programs
Businesses wishing to demonstrate their security standards to their customers and business partners can undergo auditing with a certifying body.
ISO/IEC 27K Series
The ISO/IEC 27K series provides standards for information security management, with programs covering network security, cybersecurity, and intrusion prevention.
ISO/IEC 27K is not a certification process in itself, but certain bodies are licensed to certify ISO/IEC 27K compliance.
The series consists of a family of different standards that businesses can adopt as appropriate, such as:
- ISO/IEC 27000 — Information security management systems (overview)
- ISO/IEC 27005 — Information security risk management
- ISO/IEC 27033 — IT network security
- ISO/IEC 27040 — Storage security
GDPR Certification
GDPR certification is available for organizations that wish to publicize their GDPR compliance. Certification schemes must be approved by the European Data Protection Board or a national Data Protection Authority, such as the UK Information Commissioner’s Office.
GDPR certification schemes can be general, applying to all areas of an organization’s GDPR compliance, or specific to an area of GDPR compliance, such as:
- Secure storage of personal information
- Access controls
- Internal policies and procedures
You can see Tessian’s certifications on this page: Tessian Integrations, Compatibility, and Partnerships.