Phishing is a huge threat and growing more widespread every year. Tessian research found that employees receive an average of 14 malicious emails per year. that might not sound a lot, but it soon adds up in an enterprise organizations with over 2000 employees. And it only takes one to get through.
So, what does a genuine phishing attack look like? We’re rounded up 5 REAL examples of spear phishing attacks, all detected (and prevented) by Tessian Defender. Just a note on those alerts at the top of each email. These are Defender’s in-the-moment warnings that explain exactly why the email has been flagged as suspicious.
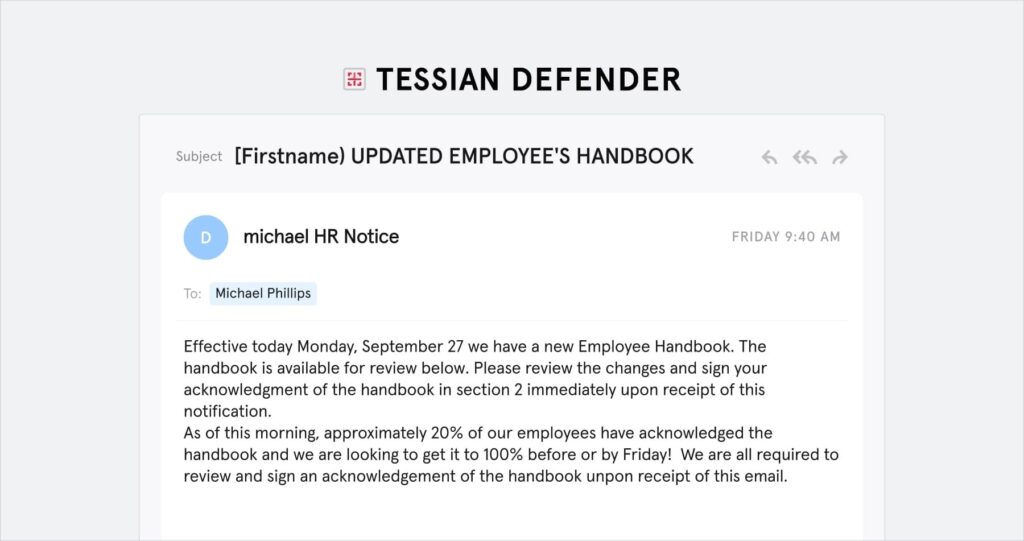
Example 1: The attacker is encouraging the target to sign an “updated employee handbook” 📋
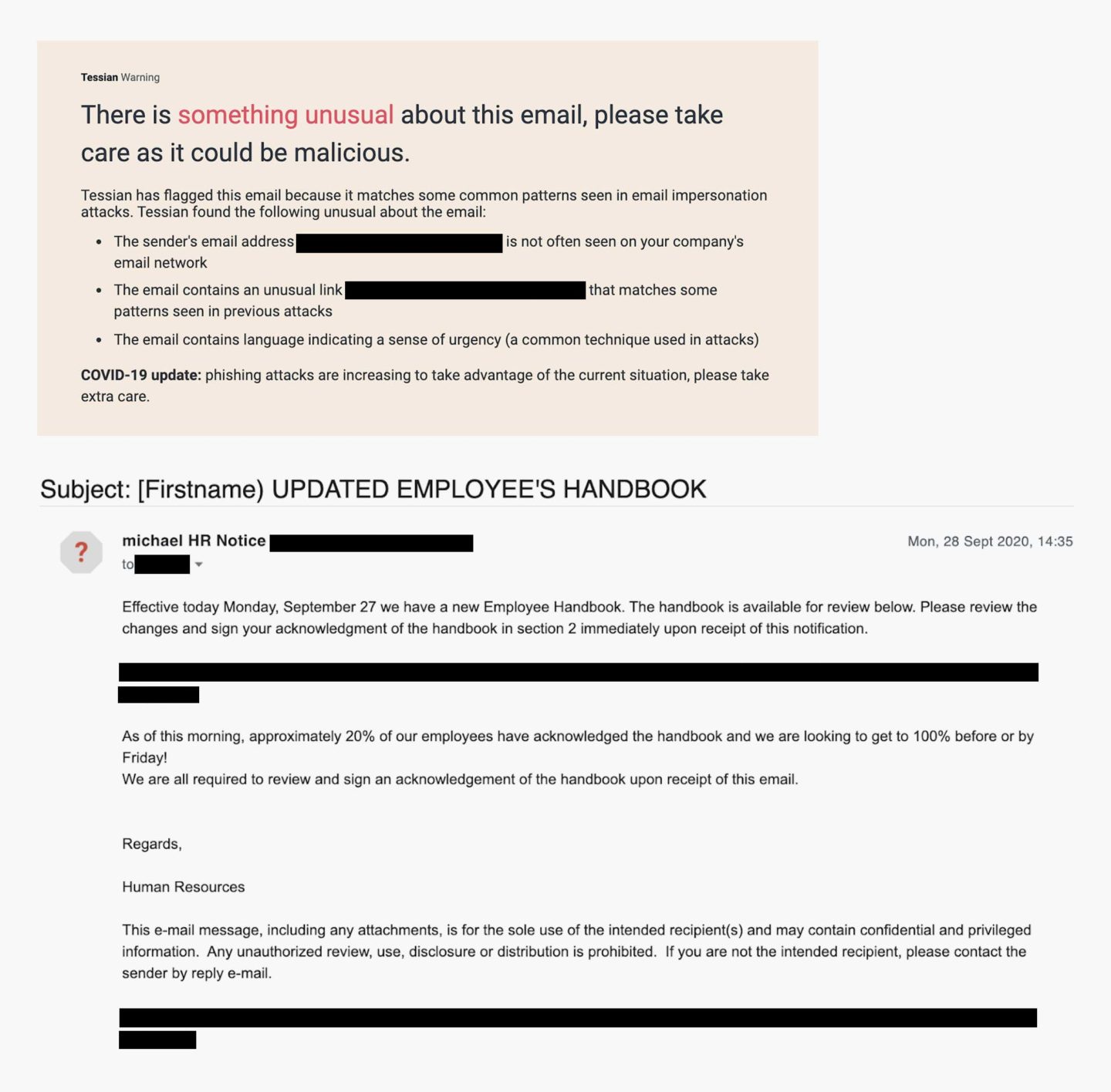
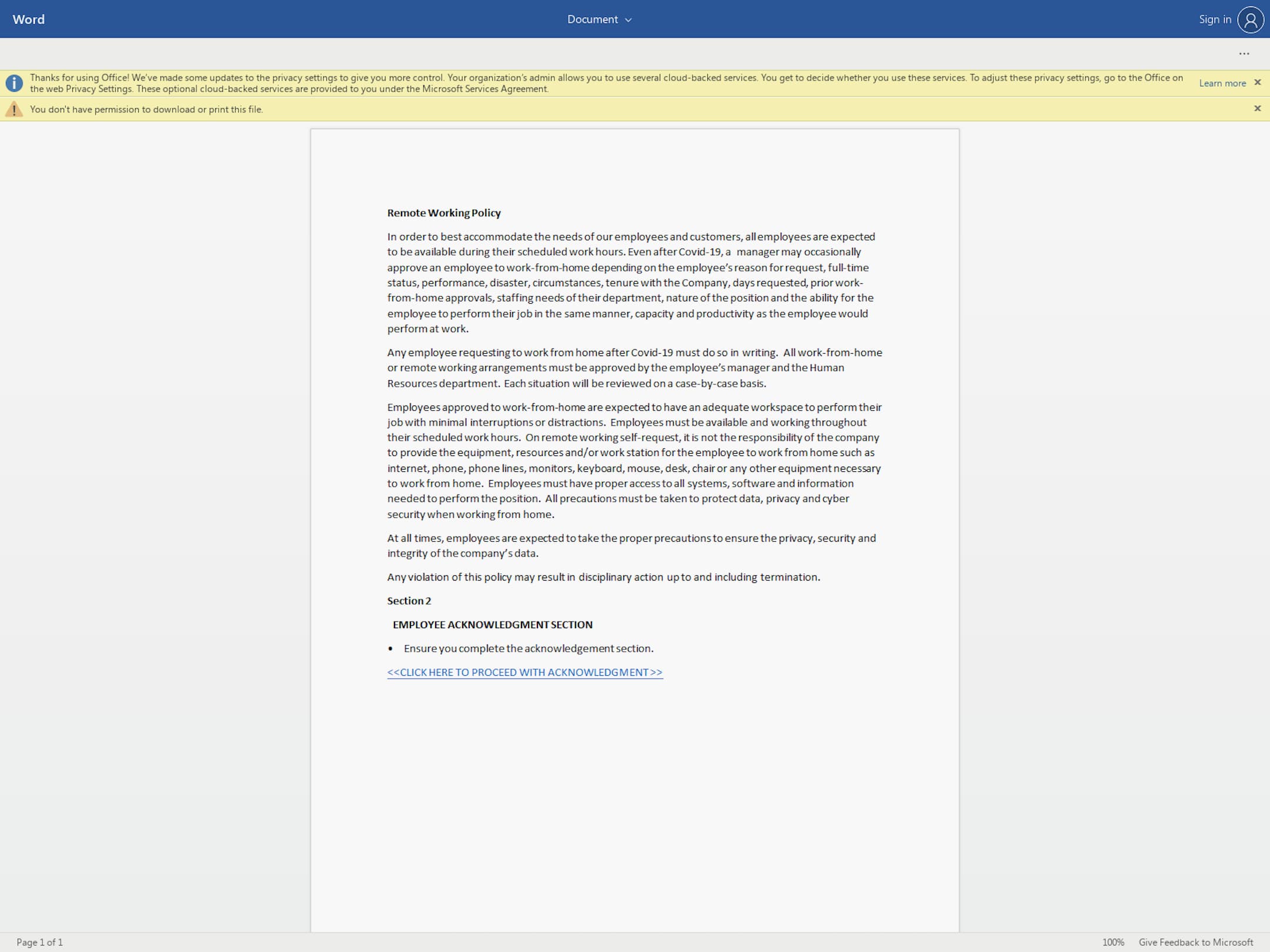
Let’s break down this spear phishing attack. In this example, the attacker is pretending to be an HR employee. But, the sender’s email address <[REDACTED]@ntlworld.com> does not match the domain of the target. In the email, the attacker is claiming that the target needs to sign a new employee handbook, and provides a link, which leads to an online Word document, see below.
This is an online document - linked in the spear phishing email - that leads users to a malicious URL.
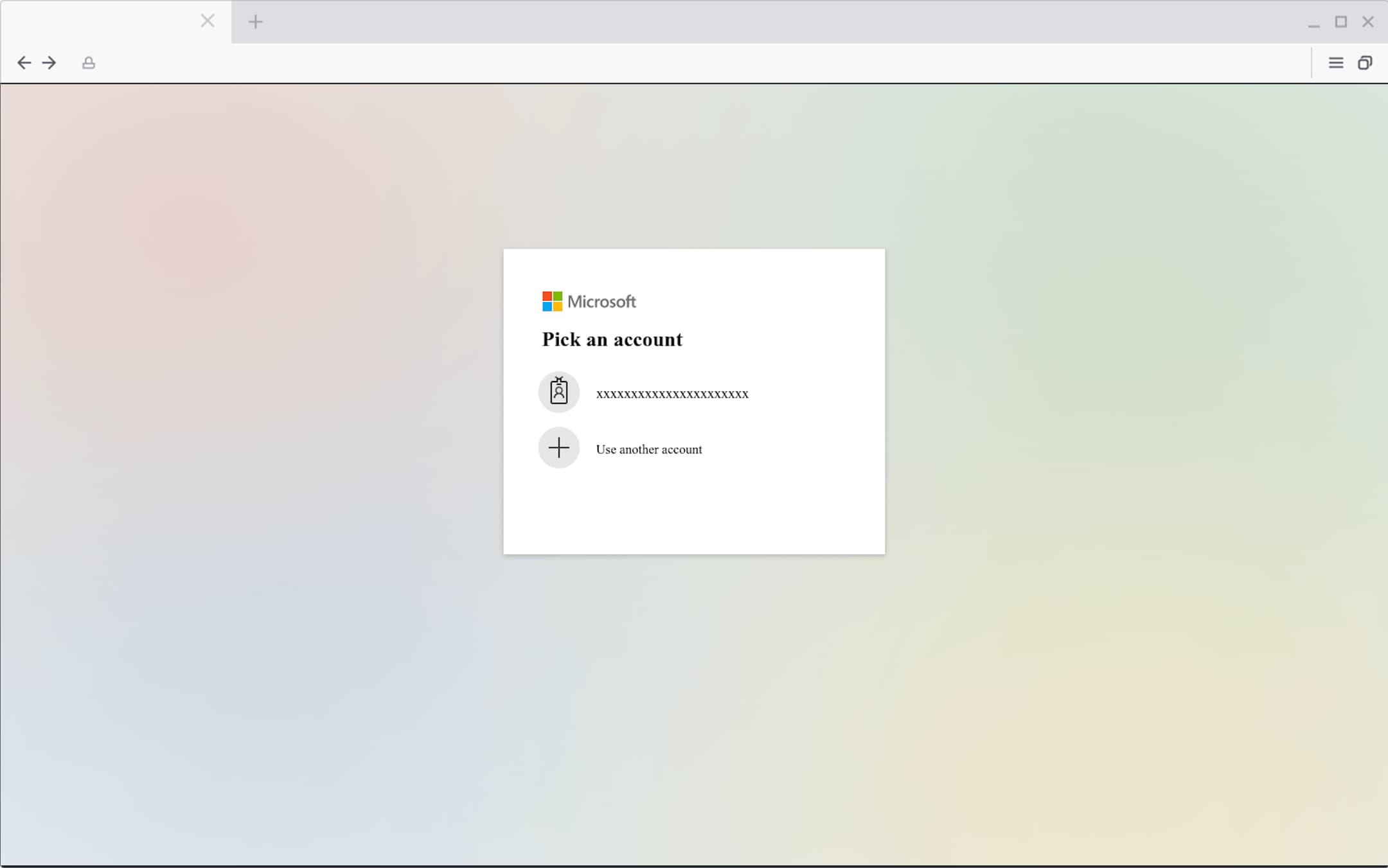
This document prompts the target to click on another link, which leads the user to a fake O365 login page. The goal: to gain access to the target’s login credentials. This is called credential phishing. The attacker is using social engineering tactics to motivate the user to act now. For example, noting that “20% of employees have already accepted” and “we are all required to review and sign an acknowledgement of the handbook upon receipt of this email”.
COVID-19 is also used as a pretext for sending the handbook in the first place, which gives legitimacy to their request.
Example 2: The email is a spoof of an MS Teams notification 🔔
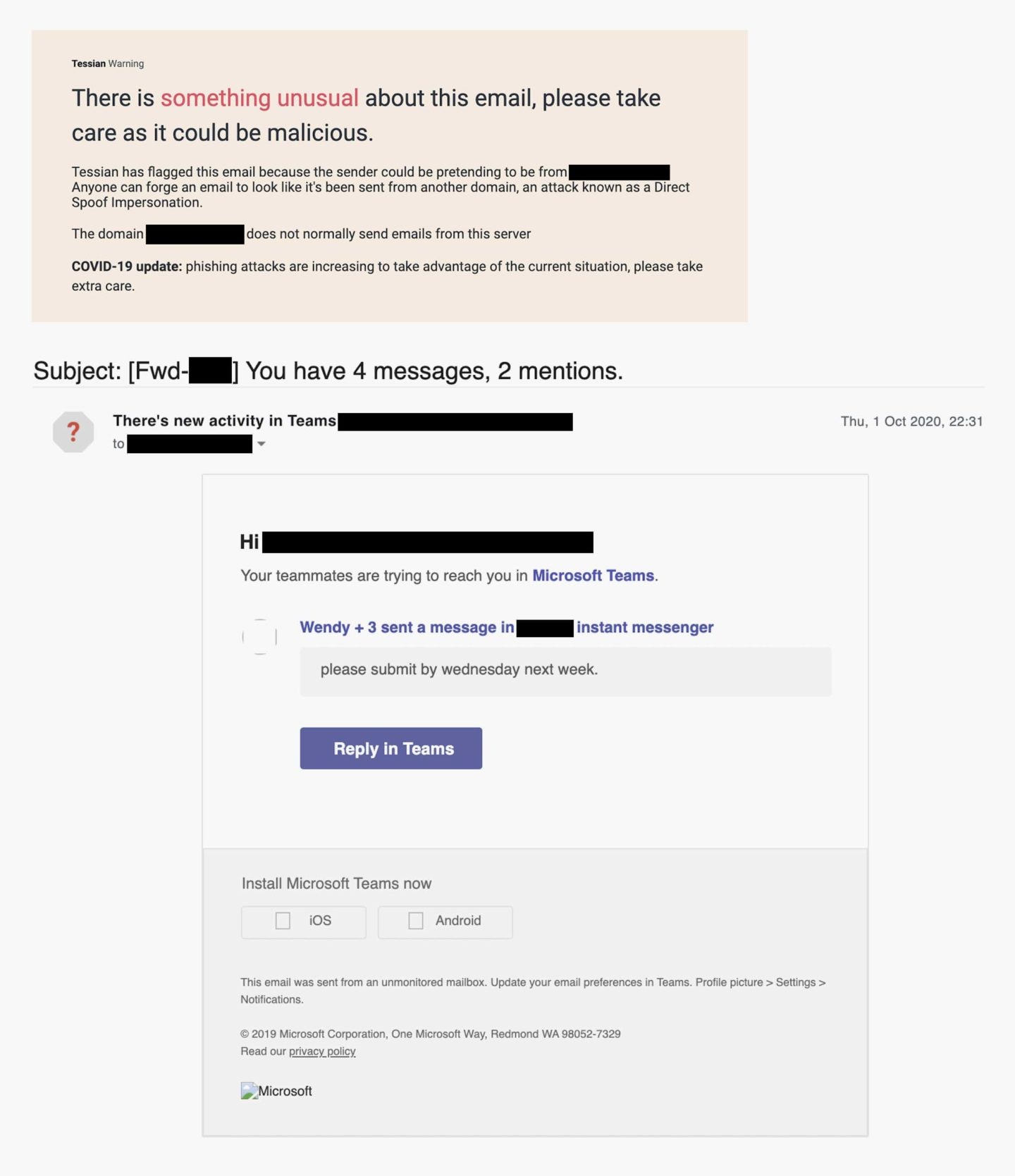
This is an example of a spear phishing email involving a fake Microsoft Teams notification.
Let’s break down this spear phishing attack. In this example, the attacker is leveraging a fake notification from a trusted platform – Microsoft Teams – instead of impersonating a trusted person/team. The goal? Credential theft. If the user clicks on the “Reply in Teams” button, they’ll be led to a fake login page.
If they enter their details, their account will be compromised. And, if the employee uses the same password for multiple accounts (which 85% of employees do), the bad actor could have access to multiple systems.
If the target follows the link in the phishing email, they'll end up here: a fake Microsoft Teams login page.
Note: Instead of seeing “xxxxxx”, the target would see their email address. Not only does this increase the legitimacy of the webpage and make the user feel like they’ve logged in before, it also reduces the friction for the user to move on to the next step, which will be entering their password.
If you actually did use Microsoft Teams at work, you’d have no reason to believe this is suspicious or malicious. The email looks like the real deal and was likely templated from a genuine notification. The email itself is a domain spoof, and spoofs the target’s own email address. This is particularly clever because – well – it’s not implausible that Microsoft Teams would actually send emails “from” the user’s own email address.
Example 3: The attacker is pretending to be a new starter 👋🏾
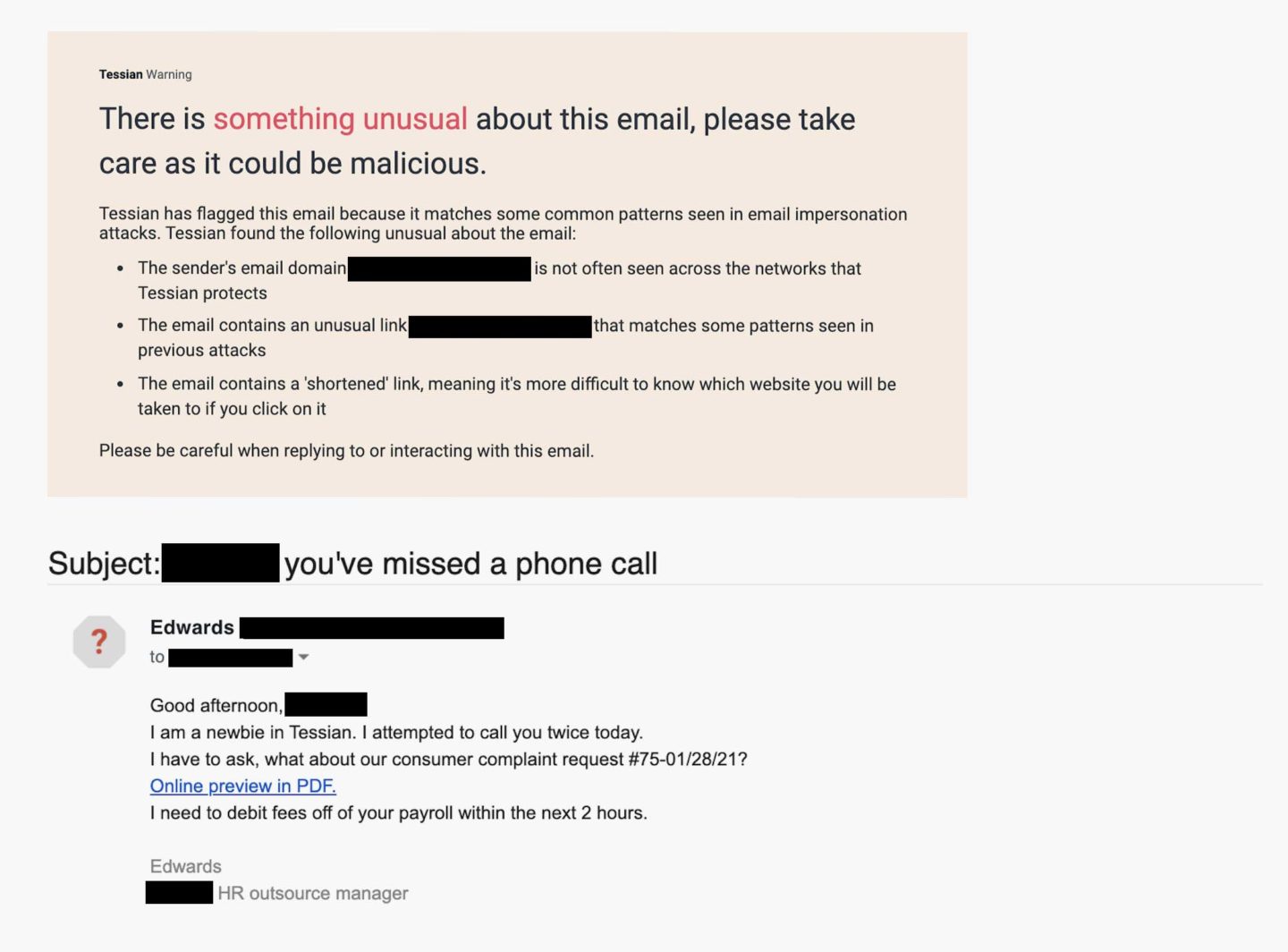
In this example, the attacker is pretending to be a new starter at the target’s company’s outsourced HR management firm. This is an especially effective social engineering tactic that preys on human kindness. Who doesn’t want to help out a newbie? The language in the email is also quite informal and friendly; this will make the target feel comfortable and lower their guard.
At face value, the email address <edwards@[REDACTED].com> isn’t suspicious. But, it may raise red flags for the target if he or she hasn’t heard from anyone with that domain before. But only 54% of employees say they look at the sender’s email address before responding to an email or actioning a request.
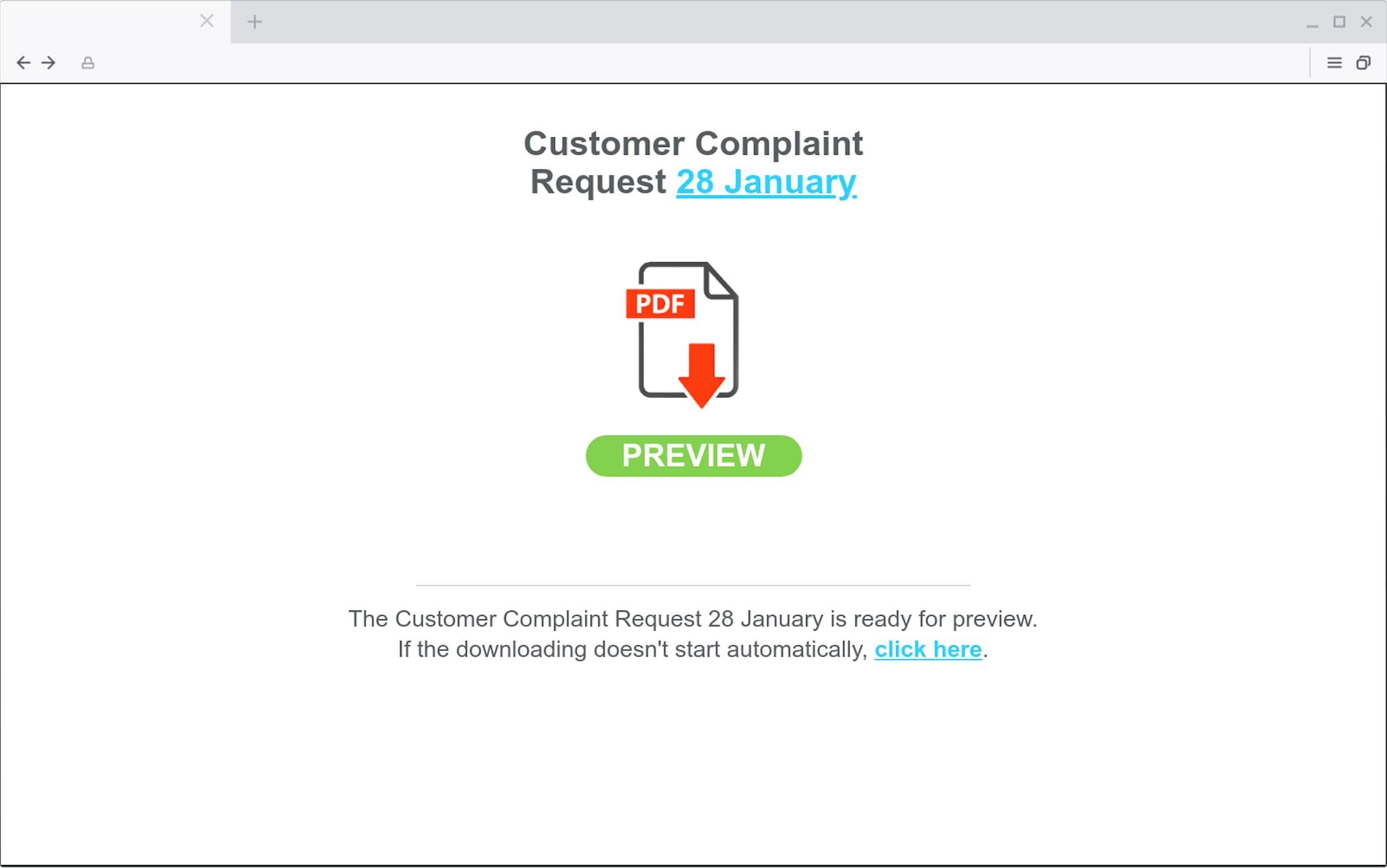
The attacker is trying to encourage the target to click on a link to preview a PDF urgently – “in the next two hours”. Tessian Defender has also flagged that this is a bitly link. Bad actors often use these shortened URLs to make it more difficult for the target to know what website they’ll be taken to if they do click. Of course, the link doesn’t lead to a PDF. It leads to a malicious website. If the target were to click the download button, malware would likely be deployed.
This is a malicious website. If the target clicks the "Preview" button, malware will likely be deployed.
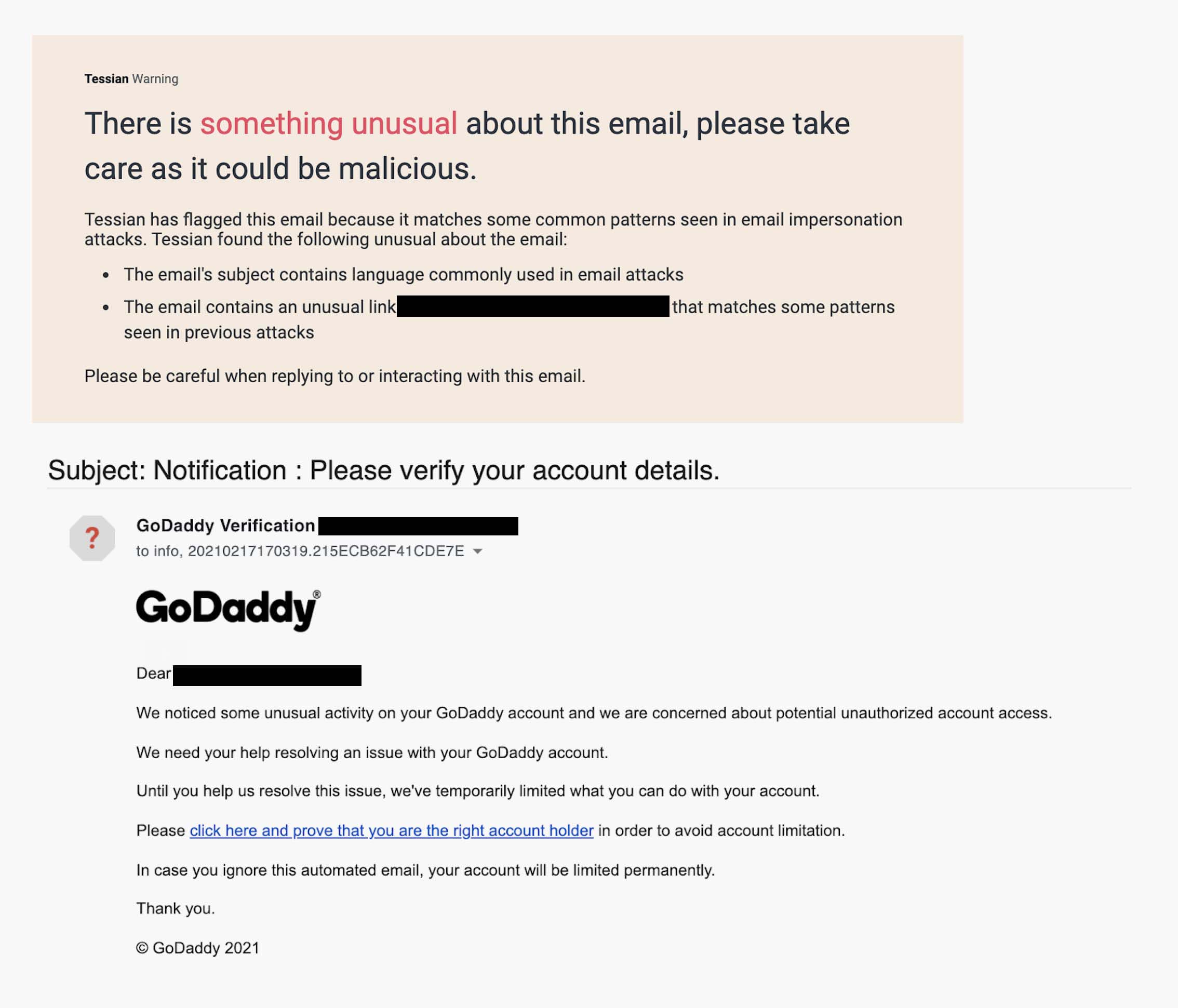
Example 4: The email claims to be verifying account activity on GoDaddy ✅
In this example of a spear phishing email, the attacker is impersonating GoDaddy.
In this example, the attacker is impersonating GoDaddy – the world’s largest domain register company, with over 40 million domain names under its management. While GoDaddy appears in the Display Name and several times in the body of the email (including a logo), and there aren’t any obvious spelling errors or grammar mistakes, a savvy employee would notice that the sender’s email address <[REDACTED]@hotmail.com> doesn’t match. Remember, though: Most employees don’t examine email addresses before responding or actioning a request.
Again, the name of the game here is credential phishing. If the target follows the link to “prove they’re the account holder” they’ll be sent to a fake GoDaddy sign-in page. If they enter their login details, their credentials will be compromised. This is an especially dangerous attack because – if an employee’s login credentials for GoDaddy were compromised – the attacker could (quite literally) take over your website. They could steal your customer’s data or even use your website to host other phishing websites.
Example 5: The email appears to be sent from the company’s Microsoft File Sharing service 📎
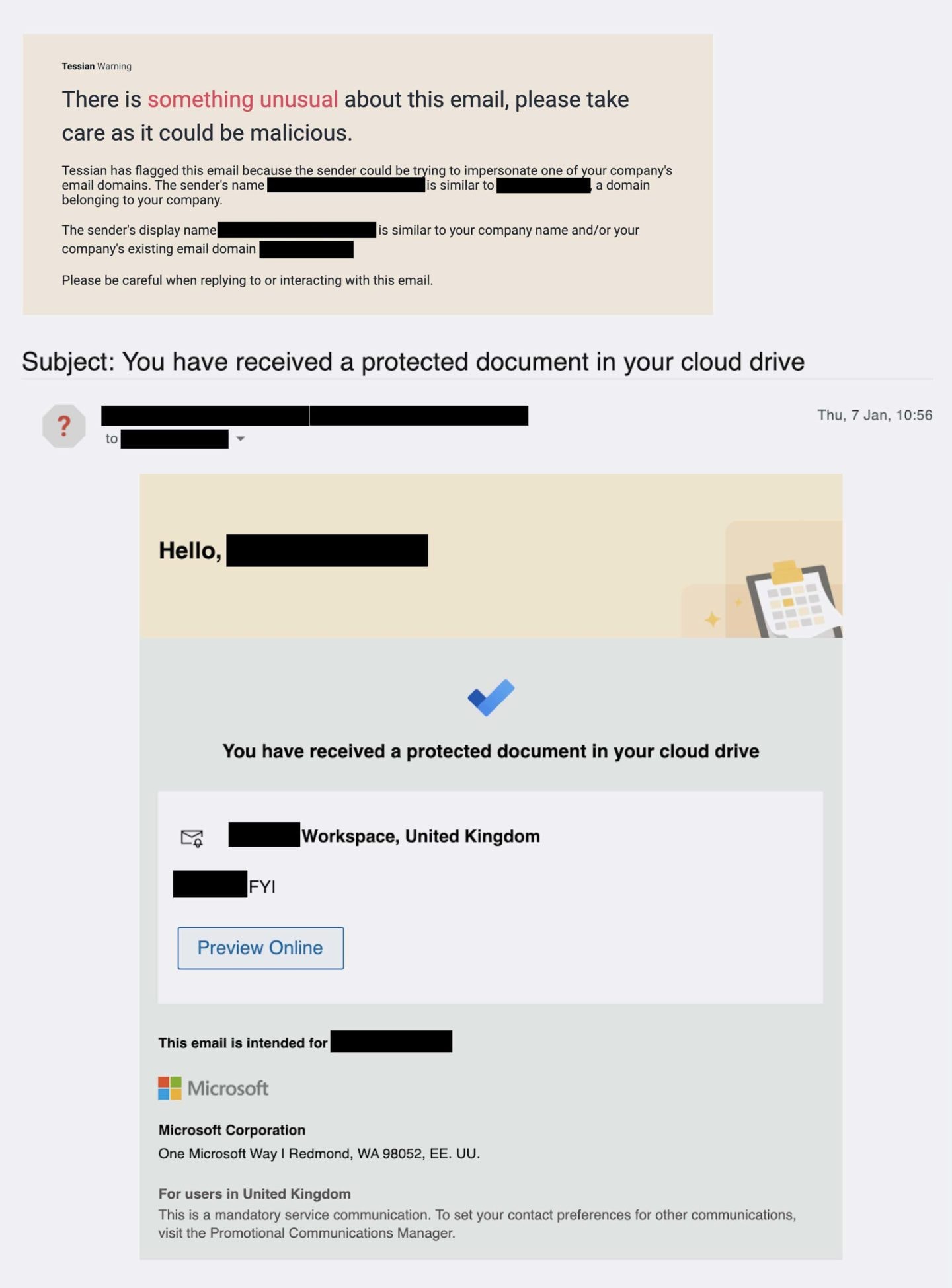
Again, in this example, the attacker is leveraging a fake notification from Microsoft. This time, though, it’s from Microsoft File Sharing service. Unsurprisingly, the attacker is after the target’s credentials. (This is called credential phishing, remember?) If the user clicks on the “Preview Online” button – a malicious link – they’ll be taken to a lookalike website.
If the target does input their credentials, they won’t login to Microsoft File Sharing. Instead, the details will be sent directly to the hacker, who will then have easy access to the user’s account. Notice that the notification is well-formatted and looks like a genuine email from Microsoft. There aren’t any obvious spelling or grammar errors. The average person would likely fall for this attack.
The “[REDACTED], FIY” note was included on purpose. The attacker is trying to pique the target’s interest. Wouldn’t you want to know what the message said? The more curious and emotional we get, the more likely we are to click a link without thinking of security.