Phishing is a decades-old social engineering attack that costs people and businesses billions each year. One small mistake can have serious consequences.
But you can take a few simple and effective steps to avoid falling for one.
This article will explain how to recognize a phishing email, how cybercriminals can leverage publicly-available information, and what technical solutions are available to help businesses prevent successful phishing attacks.
If you’d rather learn more about what phishing is, don’t worry. We can help. Read this article first: Phishing 101: What is Phishing?
Learn to recognize a phishing email
There are some hallmarks of a phishing email that you should be able to recognize.
But be careful — none of these traits are common to every phishing email, and most of them won’t be present in more sophisticated phishing campaigns.
And remember! Phishing and spear phishing are different. If you’re looking for tips to help you spot spear phishing emails, read this article instead: What Does a Spear Phishing Email Look Like? 4 Red Flags.
1. Branding
When you receive an email, ask yourself “Does this look right?” A good first step is to check for inauthentic or amateurish logos and email signatures.
Here’s an example: on the left is a genuine email from shipping company DHL, and on the right is a fake, taken from a 2020 phishing campaign:
In this side-by-side example, you can see a real email from DHL, and a phishing email that's been sent to appear like it's from DHL.
You can see that the email on the right is trying to look like DHL. It’s using DHL’s red and yellow branding, but it’s clearly a cheap imitation. If you receive an email looking like this, alarm bells should immediately start ringing.
2. Spelling and grammar
Second, check the email for spelling and grammar mistakes. Again, while poor spelling and grammar is a good indicator that an email is inauthentic, it’s increasingly common for phishing campaigns to contain very few errors.
Check out this example:
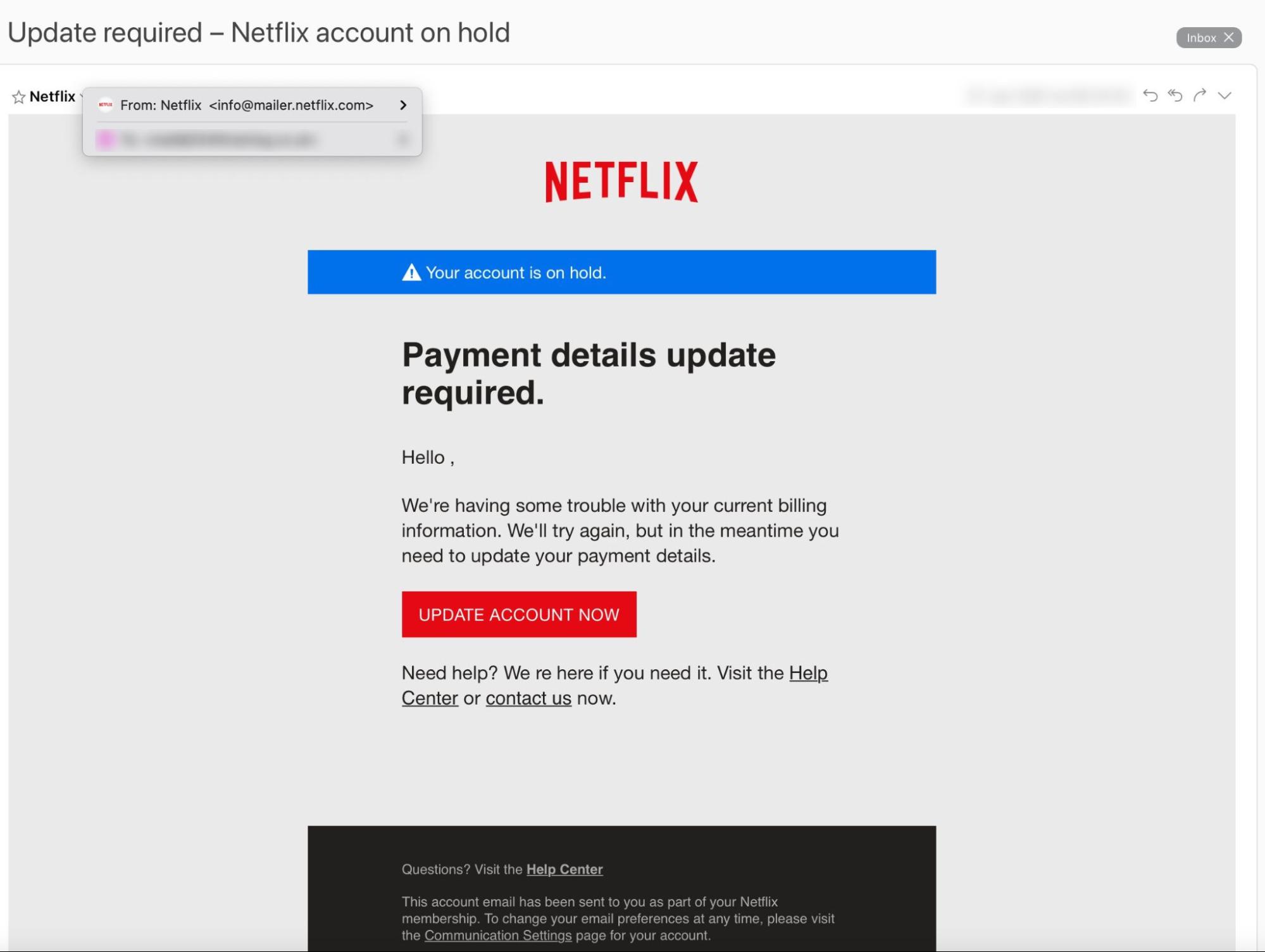
This image comes from a Netflix phishing scam that has been active since at least May 2018.
This fake Netflix email is a real-life example of a credential phishing attack that has been circulating since at least May 2018.
Not sure what credential phishing is? We explain everything you need to know in this article: What is Credential Phishing? How Does it Work?
Unlike the DHL email, this Netflix scam is pretty convincing, except for a couple of tiny errors that give it away. There’s an unnecessary space in the greeting (“Hello ,”) and a missing apostrophe (We re here if you need it).
These errors don’t necessarily indicate a phishing email — they might have gotten past Netflix’s quality control team — but they’re a red flag (if you notice them).
3. Sense of urgency
Third, a phishing attack usually conveys some sense of urgency. Whether the attacker is trying to persuade you to make a payment, download a file, or click a link — they know you’re more likely to do so if you’re feeling anxious. Stressed people make bad decisions. We explore this in detail here: The Psychology of Human Error.
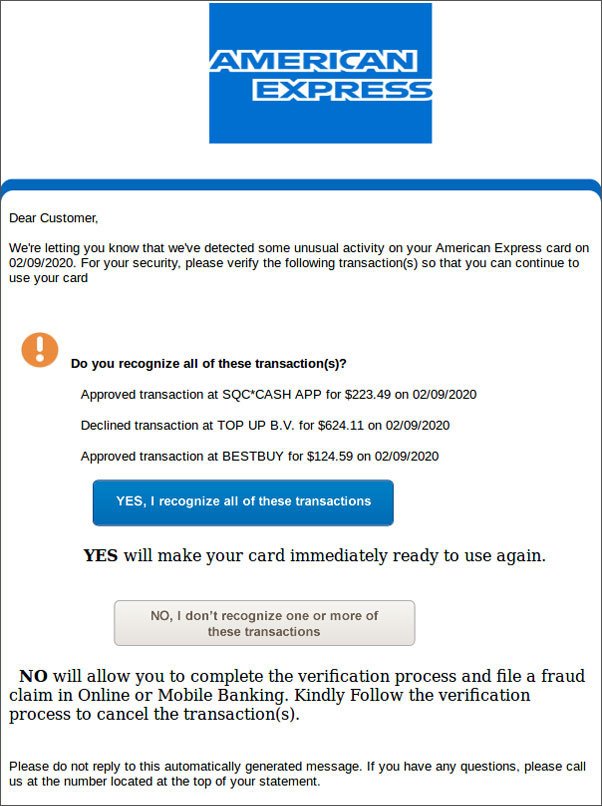
Here’s an example of an American Express scam that emerged in 2020:
This is example of an American Express phishing scam.
Many people will panic when receiving this and immediately click “NO.” They might even do this despite having second thoughts about the nature of the email. Of course, this is exactly what the cybercriminal wants.
4. Inauthentic sender address
Finally, there might be some more subtle indicators that the email you’ve received is part of a phishing scam. These have to do with the sender’s email address.
A phishing email is more likely to succeed if it appears to come from an authentic email address. This type of phishing is called Business Email Compromise (BEC), and the FBI estimates that it cost businesses $1.7 billion in 2019.
Cybercriminals use three main techniques to make email addresses look authentic:
- Email impersonation: The email looks similar to a genuine business email address (think “b.gates@micros0ft.com” or “elonmusk@tessianmail.com”). Impersonation can be easy to spot if you’re paying attention.
- Email spoofing: The fraudster amends the email’s headers, so the receiving email client displays a false address. In some cases, spoofing is only noticeable if you inspect the email header information.
- Account takeover (ATO): The email arrives from an authentic account that has been hacked. ATO is nearly impossible for a person to detect and requires email security software.
Limit your publicly available personal information
Spear phishing is a subcategory of phishing targeting a specific person by name. Cybercriminals can find your name and email address easily — but they probably have access to a lot more of your personal information, too.
According to Tessian research, 90% of people post personal and professional information online. Many employees also appear in company publicity or press releases. Even out-of-office auto-replies can give away personal information.
This information is gold dust for hackers seeking to impersonate someone the target trusts. Drop in a few personal references — whether about the target or the person the cybercriminal is impersonating — and a spear phishing email becomes a lot more persuasive.
Wondering what you should (and shouldn’t) post online? Read the full report to find out.
“Most people are very verbose about what they share online.You can find virtually anything. Even if you can’t find it publicly, it’s easy enough to create an account to social engineer details or get behind some sort of wall - for example, you could become a 'friend' in their circle.”
Harry Denley
Security and Anti-Phishing at MyCrypto
Deploy email security software
If you’re an individual looking for advice, skip this section. This piece of advice is for security and business leaders.
As we’ve seen, phishing is becoming increasingly hard for humans to spot. It’s also an email-based attack 96% of the time. That’s why deploying an intelligent inbound email security solution is the key to preventing phishing.
Email security is particularly important as teams move into a remote working environment, away from the protection of CISOs and IT departments. Microsoft research shows that 80% of security professionals saw an increase in security incidents since employees started working from home.
Phishing emails almost always carry some signals that reveal they are dangerous. The more subtle phishing indicators aren’t detectable by humans — or traditional solutions like Secure Email Gateways (SEGs) and spam filters.
Tessian Defender uses machine learning, anomaly detection, behavioral analysis, and natural language processing to detect even the most discrete phishing signals.
Click here to learn more about how Tessian Defender protects your team from phishing and other email-based cybersecurity attacks. You can also explore our customer stories to see how they’re using Tessian Defender to protect their people on email and prevent social engineering attacks like phishing.