Tessian Blog
Subscribe to our blog
Industry insights, straight to your inbox every week
- All Categories
- ...
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityEmail is the #1 Threat Vector. Here’s Why.
-
 Integrated Cloud Email Security
Integrated Cloud Email Security5 Cybersecurity Stats You Didn’t Know (But Should)
-
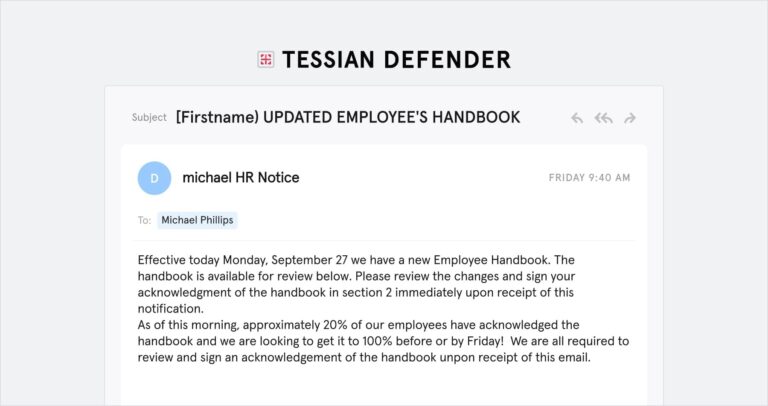 Advanced Email Threats
Advanced Email ThreatsReal Spear Phishing Examples and Why They Worked
-
 Interviews With CISOs
Interviews With CISOsRelationship 15: A Framework to Help Security Leaders Influence Change
-
 Integrated Cloud Email Security
Integrated Cloud Email Security7 Things We Learned at Tessian Human Layer Security Summit
-
 Life at Tessian, Engineering Blog
Life at Tessian, Engineering BlogEarly adoption: Is Now the Time to Invest in the ‘New Breed’ of Security Products?
-
 Advanced Email Threats
Advanced Email ThreatsAttackers are Using Microsoft Forms to Exfiltrate Data
-
 Advanced Email Threats
Advanced Email ThreatsWhat is Spear Phishing? Targeted Phishing Attacks Explained
-
 Customer Stories
Customer StoriesHow Tessian Gave GoCardless Better Control and Visibility of Their Email Threats
-
 Advanced Email Threats
Advanced Email ThreatsHow to Avoid Falling For a Phishing Attack
-
 Advanced Email Threats
Advanced Email ThreatsHow Hackers Are Exploiting The COVID-19 Vaccine Rollout
-
 Advanced Email Threats
Advanced Email ThreatsCOVID-19: Screenshots of Phishing Emails
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsRomance Fraud Scams Are On The Rise
-
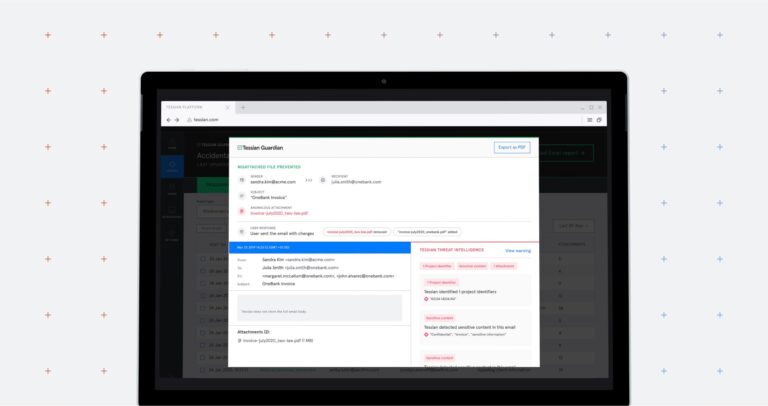 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email SecurityIndustry-First Product: Tessian Now Prevents Misattached Files on Email
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityCheck out the Speaker Line-Up for Tessian Human Layer Security Summit!
-
 Email DLP, Insider Risks
Email DLP, Insider Risks12 Examples of Data Exfiltration
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityThe 7 Deadly Sins of SAT
-
 Integrated Cloud Email Security
Integrated Cloud Email SecuritySAT is Dead. Long Live SAT.
-
 Advanced Email Threats
Advanced Email Threats6 Reasons to Download “How to Hack a Human” Now
-
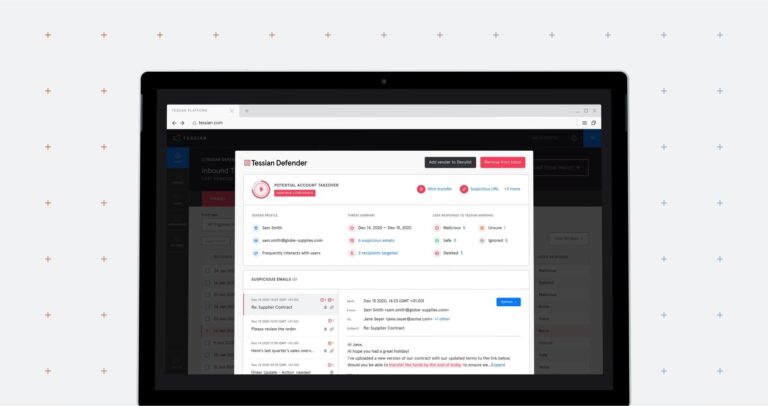 Advanced Email Threats
Advanced Email ThreatsTessian Launches Account Takeover (ATO) Protection







