Advanced Email Threats
Get up to speed on the latest tips, guides, industry news and technology developments around phishing, spear phishing, Business Email Compromise, and Account Takeover
- All Categories
- ...
-
 Advanced Email Threats, Product Updates
Advanced Email Threats, Product UpdatesTessian stopped over 3,000 QR code phishing attacks in just 1 day
-
 Integrated Cloud Email Security, Beyond the SEG / Microsoft + Tessian, Advanced Email Threats, Security Awareness Coaching
Integrated Cloud Email Security, Beyond the SEG / Microsoft + Tessian, Advanced Email Threats, Security Awareness CoachingLatest Microsoft Report Confirms Need for AI-Based Phishing Protection
-
 Advanced Email Threats, Product Updates
Advanced Email Threats, Product UpdatesUnlock Email Security Visibility Within Splunk
-
 Beyond the SEG / Microsoft + Tessian, Advanced Email Threats
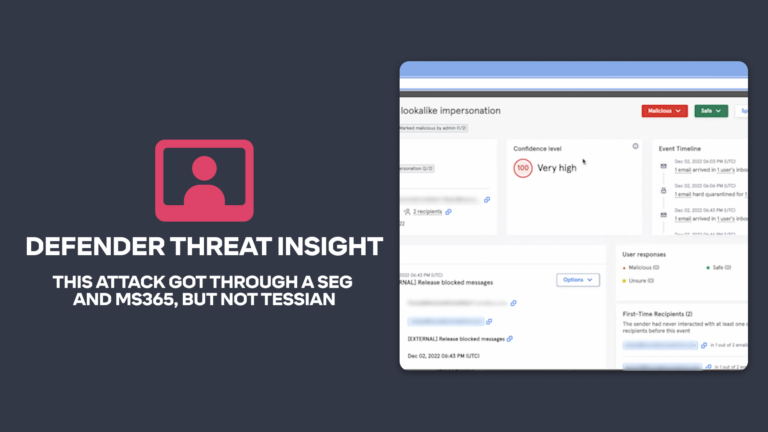
Beyond the SEG / Microsoft + Tessian, Advanced Email ThreatsTessian in Action: This Attack Got Through a SEG and M365, but Not Tessian.
-
 Advanced Email Threats
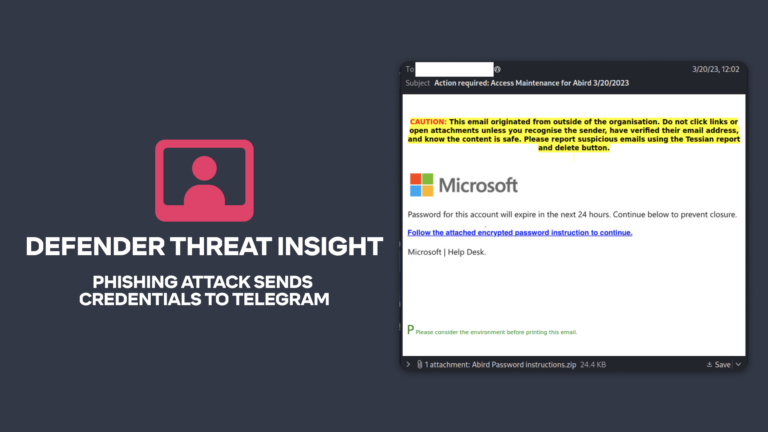
Advanced Email ThreatsTessian in Action: Phishing Attack Sends Credentials to Telegram
-
 Beyond the SEG / Microsoft + Tessian, Advanced Email Threats, Threat Stories
Beyond the SEG / Microsoft + Tessian, Advanced Email Threats, Threat StoriesTessian in Action: Microsoft Credential Scraping Attempt
-
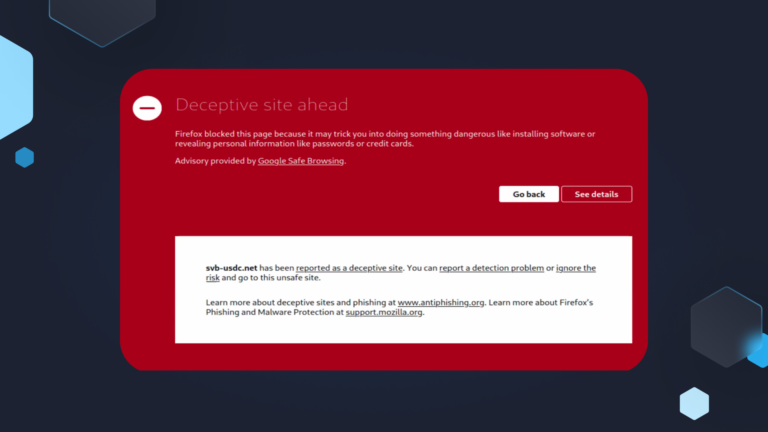 Attack Types, Advanced Email Threats, Threat Stories
Attack Types, Advanced Email Threats, Threat StoriesDozens of SVB and HSBC-themed URLs Registered
-
 Attack Types, Advanced Email Threats, Threat Stories
Attack Types, Advanced Email Threats, Threat StoriesThe Current SVB Banking Crisis Will Increase Cyberattacks, Here’s How to Prepare
-
 Beyond the SEG / Microsoft + Tessian, Advanced Email Threats
Beyond the SEG / Microsoft + Tessian, Advanced Email ThreatsWhy You Should Download the Microsoft 365 + Tessian Guide
-
 Advanced Email Threats, Compliance
Advanced Email Threats, ComplianceWill Australia’s Tougher Cyber Regulation Force Firms to Upgrade Their Security?
-
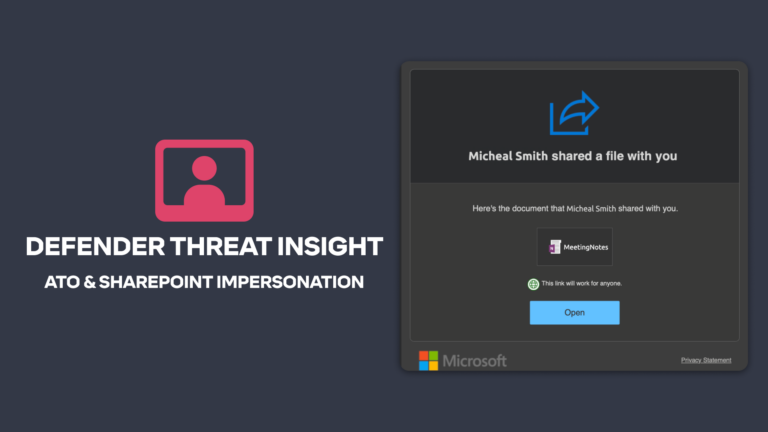 Advanced Email Threats
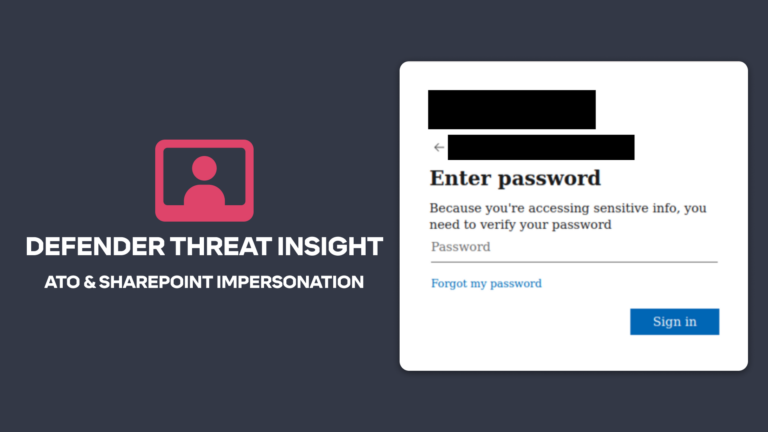
Advanced Email ThreatsTessian in Action: Account Takeover & SharePoint File Share Attack
-
 Email DLP, Attack Types, Advanced Email Threats, Insider Risks
Email DLP, Attack Types, Advanced Email Threats, Insider RisksPreventing ePHI Breaches over Email for Healthcare Organizations
-
 Email DLP, Integrated Cloud Email Security, Advanced Email Threats
Email DLP, Integrated Cloud Email Security, Advanced Email ThreatsSecure Email Gateways (SEGs) vs. Integrated Cloud Email Security (ICES) Solutions
-
 Advanced Email Threats
Advanced Email Threats15 Examples of Real Social Engineering Attacks
-
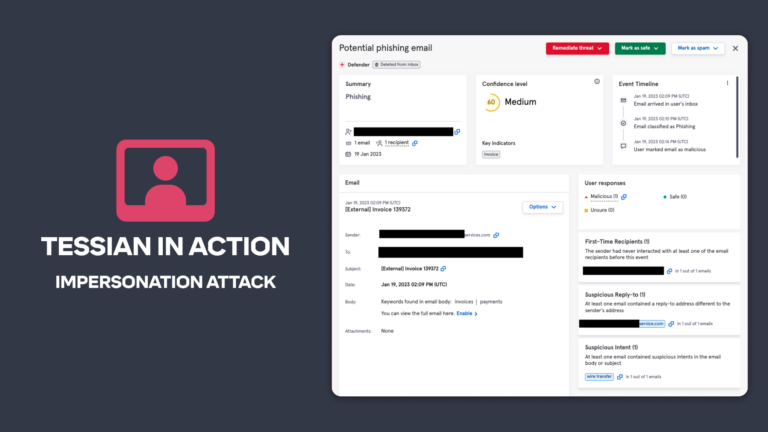 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsTessian in Action: Stopping an Impersonation Attack
-
 Advanced Email Threats
Advanced Email ThreatsThe Time for Cloud Email Security is Now: Microsoft 365 + Tessian
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsHow Tessian stops Impersonation Attacks
-
 Advanced Email Threats, Threat Stories
Advanced Email Threats, Threat StoriesTessian Threat Intel Roundup: Advanced Phishing Attacks
-
 Advanced Email Threats
Advanced Email ThreatsBoard Members Believe Their Companies Are Unprepared For A Cyberattack
-
 Email DLP, Advanced Email Threats, Insider Risks
Email DLP, Advanced Email Threats, Insider RisksWhat is email security and why it’s important







