Advanced Email Threats
Get up to speed on the latest tips, guides, industry news and technology developments around phishing, spear phishing, Business Email Compromise, and Account Takeover
- All Categories
- ...
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email Threats1 in 5 Chief Information Security Officers (CISOs) Work More Than 25 Extra Hours Per Week
-
 Advanced Email Threats, Remote Working, Insider Risks
Advanced Email Threats, Remote Working, Insider RisksCybersecurity Awareness Month 2022: 12+ Free Resources
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsProduct Update: Enhanced Security Event Filtering and Reporting
-
 Advanced Email Threats
Advanced Email ThreatsThe Three Biggest Problems Facing Law Firm Security Leaders Right Now
-
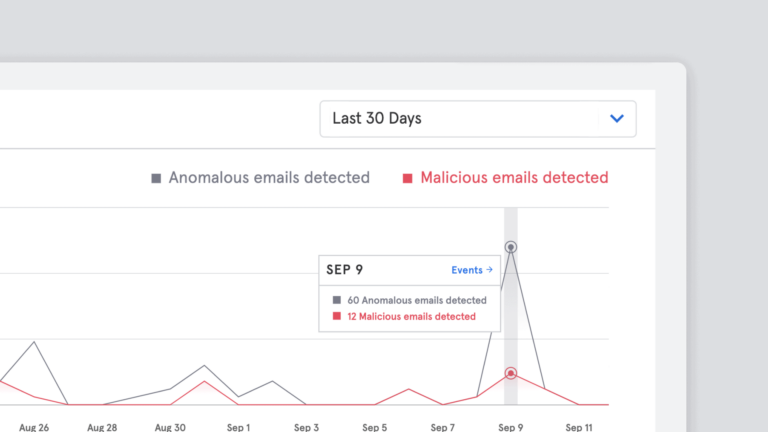 Integrated Cloud Email Security, Data & Trends, Advanced Email Threats
Integrated Cloud Email Security, Data & Trends, Advanced Email ThreatsProduct Update: Improvement to Algorithms Sees 15% Increase in Detection of Advanced Email Threats
-
 Advanced Email Threats
Advanced Email ThreatsWhen a Breach is More Than Just a Breach
-
 Advanced Email Threats
Advanced Email Threats52% of U.S. Healthcare Insurance Providers At Risk of Email Impersonation During Open Enrollment
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsKey Takeaways from IBM’s 2022 Cost of a Data Breach Report
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsHow to Prepare for Increasing Cyber Risk
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats
Integrated Cloud Email Security, Email DLP, Advanced Email ThreatsWhat is an Integrated Cloud Email Security (ICES) Solution?
-
 Advanced Email Threats
Advanced Email ThreatsHow Bad Actors Are Using the Cost of Living Crisis to Launch Attacks
-
 Advanced Email Threats
Advanced Email ThreatsTessian Threat Intel Advisory: PayPal Email Invoice Fraud Detected
-
 Advanced Email Threats, Compliance
Advanced Email Threats, ComplianceBuilding a Recession Proof Cybersecurity Program
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsKey Takeaways from Verizon’s 2022 Data Breach Investigation Report
-
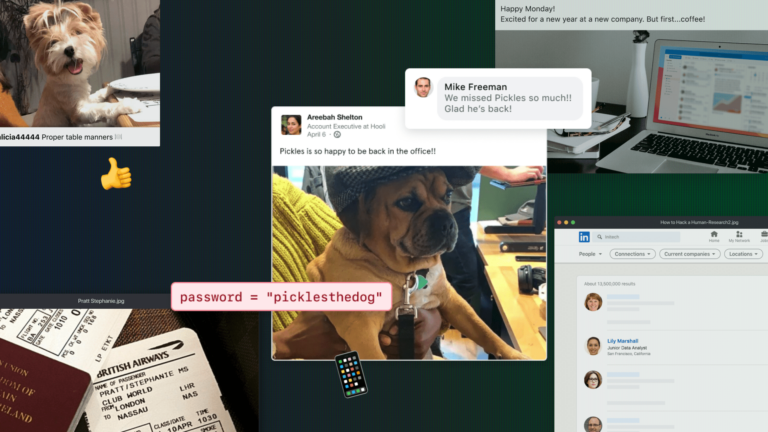 Advanced Email Threats
Advanced Email ThreatsHow Hackers Use Social Media For Phishing Attacks
-
Advanced Email Threats
Phishing Awareness Training: How Effective is Security Training?
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsFive Ways Tessian Cloud Email Security Improves Enterprise Cybersecurity
-
 Advanced Email Threats
Advanced Email ThreatsWhy You Should Stop Phishing Your Own Employees
-
 Advanced Email Threats
Advanced Email ThreatsWhy Cybercrime is Thriving, And What You Can Do About It
-
 Advanced Email Threats, Threat Stories
Advanced Email Threats, Threat StoriesPhishing Campaigns Pick-Up in the Wake of the Ukraine Invasion







