Email DLP
- All Categories
- ...
-
 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email Security451 Research: Tessian Uses Machine Learning for Better DLP
-
 Email DLP
Email DLPThe Drawbacks of Traditional DLP on Email
-
Email DLP, Compliance
5 Things Every CISO Should Know About CCPA’s Impact on Their InfoSec Programs
-
 Email DLP
Email DLPHow to Communicate Cybersecurity ROI to Your CEO
-
Email DLP, Integrated Cloud Email Security, Insider Risks
How Can Organizations Empower People to Prevent Data Exfiltration?
-
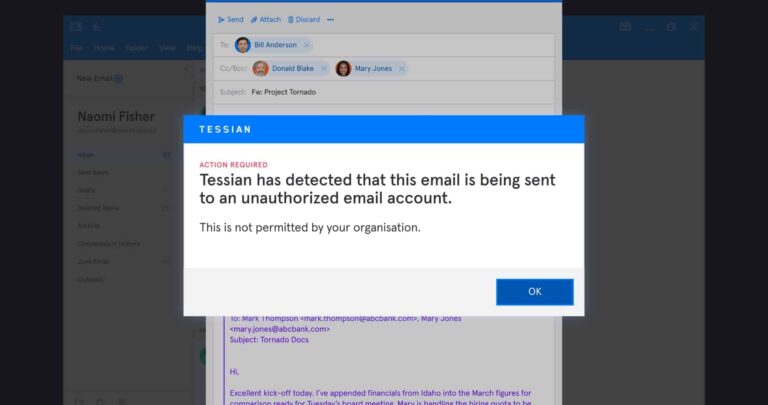 Email DLP
Email DLPHow Does Data Loss Prevention for Email Work?
-
 Email DLP
Email DLPData Privacy Day: Why You Need to Protect Your People
-
 Email DLP, Integrated Cloud Email Security, Customer Stories
Email DLP, Integrated Cloud Email Security, Customer StoriesInsights on Human Layer Security from Tim Fitzgerald, CISO of Arm
-
 Email DLP
Email DLPHow a Gmail Design Flaw Causes Misdirected Emails
-
 Email DLP
Email DLPA Brief History of Data Loss Prevention Solutions
-
 Email DLP, Integrated Cloud Email Security, Advanced Email Threats
Email DLP, Integrated Cloud Email Security, Advanced Email ThreatsA Year in Review: 2019 Product Updates
-
 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email SecurityThe Dark Side of Sending Work Emails “Home”
-
 Email DLP
Email DLPTessian Recognized as “2018 Market Leader” for Email and Data Protection
-
 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email SecurityTessian recognized as “2018 Market Leader” for Email and Data Protection
-
 Email DLP
Email DLPAutocomplete Mistake on Email
-
 Email DLP
Email DLPBupa Fined £175,000: The Risks and Costs of Unauthorized Emails







