Integrated Cloud Email Security
- All Categories
- ...
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider RisksInsider Threat Indicators: 11 Ways to Recognize an Insider Threat
-
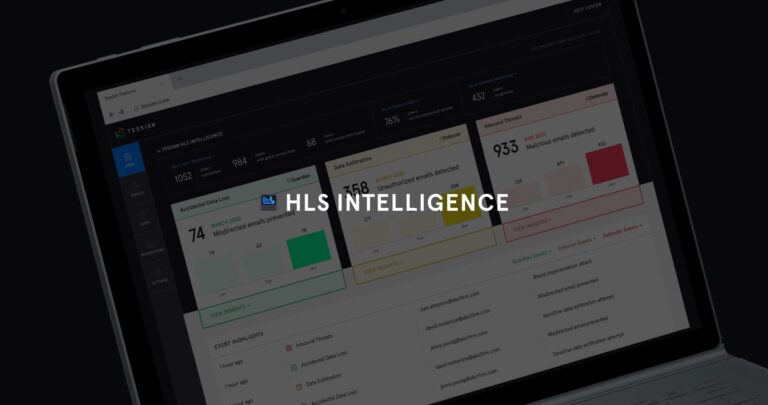 Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider RisksIntroducing Tessian Human Layer Security Intelligence
-
 Integrated Cloud Email Security, Email DLP
Integrated Cloud Email Security, Email DLPTessian Recognized by 451 Research as a “451 Firestarter”
-
 Integrated Cloud Email Security, Email DLP
Integrated Cloud Email Security, Email DLPGuide: How to Stop Data Loss Across 1 Million New Offices
-
 Integrated Cloud Email Security, Email DLP
Integrated Cloud Email Security, Email DLPThe State of Data Loss Prevention 2020: What You Need to Know
-
 Integrated Cloud Email Security
Integrated Cloud Email Security7 Reasons to Attend Tessian Virtual Human Layer Security Summit
-
 Integrated Cloud Email Security, Compliance
Integrated Cloud Email Security, ComplianceTwo Years Later: 3 Ways GDPR Has Affected Cybersecurity
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityTessian Named a Gartner Cool Vendor
-
 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email Security451 Research: Tessian Uses Machine Learning for Better DLP
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityEd Bishop Joins SecureWorld “Emerging Threats” Panel
-
 Integrated Cloud Email Security
Integrated Cloud Email Security5 Key Takeaways Tessian’s VentureBeat Webinar
-
Integrated Cloud Email Security, Email DLP, Insider Risks
How Can Organizations Empower People to Prevent Data Exfiltration?
-
 Integrated Cloud Email Security, Customer Stories
Integrated Cloud Email Security, Customer StoriesCybersecurity Awareness Should Be People-Centric, Too
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityHow to Create an Enduring and Flexible Cybersecurity Strategy
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsHacker’s Advice: 7 Tips for Avoiding Phishing Scams
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityInsights from Tessian Human Layer Security Summit | London 2020
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityRSA Recap: The Human Element is More Than a Buzzword
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityTo protect people, we need a different type of machine learning
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsTim Sadler on Hacking Humans Podcast: Episode 87 “The Art of Cheating”
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityTessian Human Layer Security Summit: Meet the Speakers







