Integrated Cloud Email Security
- All Categories
- ...
-
 Email DLP, Integrated Cloud Email Security, Insider Risks
Email DLP, Integrated Cloud Email Security, Insider Risks11 Examples of Data Breaches Caused By Misdirected Emails
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityEmail is the #1 Threat Vector. Here’s Why.
-
 Integrated Cloud Email Security
Integrated Cloud Email Security5 Cybersecurity Stats You Didn’t Know (But Should)
-
 Integrated Cloud Email Security
Integrated Cloud Email Security7 Things We Learned at Tessian Human Layer Security Summit
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsRomance Fraud Scams Are On The Rise
-
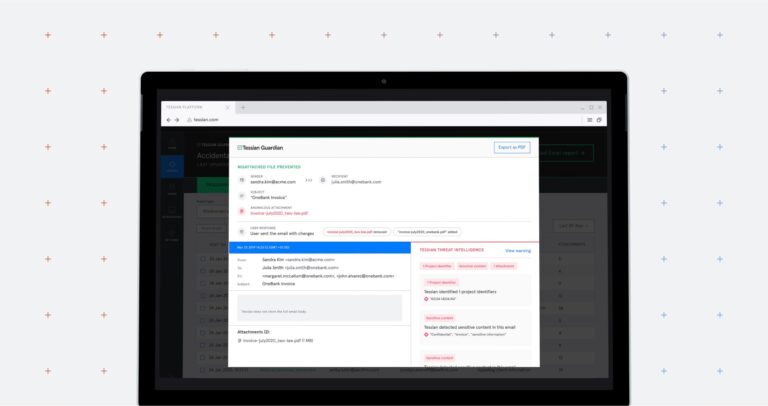 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email SecurityIndustry-First Product: Tessian Now Prevents Misattached Files on Email
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityCheck out the Speaker Line-Up for Tessian Human Layer Security Summit!
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityThe 7 Deadly Sins of SAT
-
 Integrated Cloud Email Security
Integrated Cloud Email SecuritySAT is Dead. Long Live SAT.
-
 Integrated Cloud Email Security, Podcast
Integrated Cloud Email Security, PodcastEpisode 4: The Fear Factor with Dr. Karen Renaud and Dr. Mark Dupuis
-
 Integrated Cloud Email Security, Podcast
Integrated Cloud Email Security, Podcast6 Cybersecurity Podcasts to Listen to Now
-
 Integrated Cloud Email Security, Podcast
Integrated Cloud Email Security, PodcastEpisode 3: Security For The People, Not To The People, With Tim Fitzgerald
-
Email DLP, Integrated Cloud Email Security, Advanced Email Threats, Insider Risks
Worst Email Mistakes at Work and How to Fix Them
-
 Integrated Cloud Email Security, Podcast
Integrated Cloud Email Security, PodcastPodcast Episode 2: We Just Accelerated The Future By A Decade, With Stephane Kasriel
-
 Integrated Cloud Email Security, Podcast
Integrated Cloud Email Security, PodcastPodcast Episode 1: Why Culture Trumps Strategy, With Howard Schultz
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityA Year in Review: 2020 Product Updates
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityNovember Cybersecurity News Roundup
-
 Integrated Cloud Email Security, Compliance
Integrated Cloud Email Security, Compliance10 Reasons Why CEOs Should Care About Cybersecurity
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityWhat Does 2021 Hold for Cybersecurity? Here Are Tessian’s Predictions
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityTessian Webinar Recap: Cybersecurity Insights to Influence Your 2021 Strategy







