Integrated Cloud Email Security
- All Categories
- ...
-
 Integrated Cloud Email Security, Customer Stories
Integrated Cloud Email Security, Customer StoriesRecap: Tessian Webinar, How to Build a Security Culture in Today’s Working World
-
 Integrated Cloud Email Security, Customer Stories
Integrated Cloud Email Security, Customer StoriesRecap: Q&A With Chris Kovel, CTO, PJT Partners
-
 Integrated Cloud Email Security, Interviews With CISOs
Integrated Cloud Email Security, Interviews With CISOsRecap: Tessian Webinar, Can Automation Supercharge Your IT Team?
-
 Email DLP, Integrated Cloud Email Security, Advanced Email Threats, Insider Risks
Email DLP, Integrated Cloud Email Security, Advanced Email Threats, Insider RisksOctober Cybersecurity News Roundup
-
 Email DLP, Integrated Cloud Email Security, Advanced Email Threats, Insider Risks
Email DLP, Integrated Cloud Email Security, Advanced Email Threats, Insider RisksTessian Included as a Cloud Email Security Supplement Solution in Gartner’s 2020 Market Guide for Email Security
-
Integrated Cloud Email Security
20 Virtual Cybersecurity Events To Attend in 2020 (Updated September)
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsTim Sadler on Hacking Humans Podcast: Ep 117 “It’s Human Nature”
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityHuman Layer Security Summit On-Demand: 5 Sessions to Watch Now
-
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks, Compliance, Customer Stories
18 Actionable Insights From Tessian Human Layer Security Summit
-
Integrated Cloud Email Security, Life at Tessian
Why Customer Centricity is So Important At Tessian
-
Integrated Cloud Email Security, Email DLP, Customer Stories
9 Questions That Will Help You Choose The Right Email Security Solution
-
Integrated Cloud Email Security
8 Reasons To Register Now For Tessian Human Layer Security Summit
-
Email DLP, Integrated Cloud Email Security, Advanced Email Threats, Insider Risks
Research Shows Employee Burnout Could Cause Your Next Data Breach
-
 Integrated Cloud Email Security, Email DLP, Customer Stories
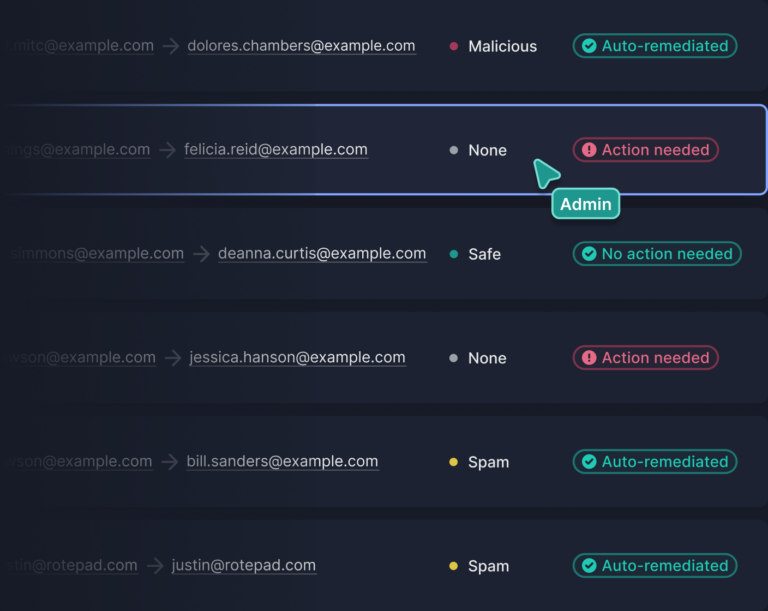
Integrated Cloud Email Security, Email DLP, Customer StoriesData Leakage and Exfiltration: 7 Problems Tessian Helps Solve
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider RisksResearch Shows How To Prevent Mistakes Before They Become Breaches
-
Integrated Cloud Email Security
Tessian included in Forrester Now Tech: Enterprise Email Security Providers, Q3 2020 report
-
 Email DLP, Integrated Cloud Email Security, Insider Risks
Email DLP, Integrated Cloud Email Security, Insider RisksResearch Shows Employees Are Less Likely To Follow Safe Data Practices At Home
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats
Integrated Cloud Email Security, Email DLP, Advanced Email ThreatsTessian Human Layer Security Summit: Your Questions, Answered
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityHow to Adapt: 7 Tips from Upwork’s Former CEO
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Customer Stories
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Customer Stories13 Things We Learned at Tessian Virtual Human Layer Security Summit







