Tessian Blog
Subscribe to our blog
Industry insights, straight to your inbox every week
- All Categories
- ...
-
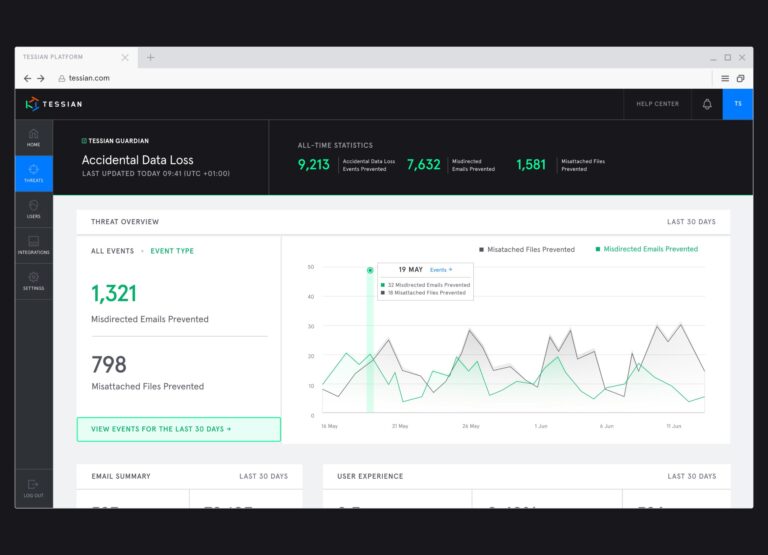 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Sara Zahid From Jefferies
-
 Email DLP
Email DLPData Privacy Day: Why You Need to Protect Your People
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Tess Frieswick From Kivu
-
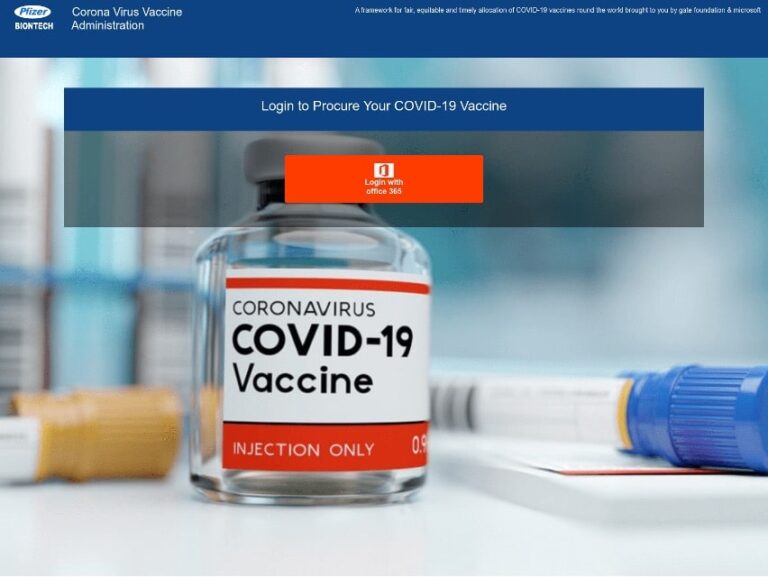 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Carolann Shields From KPMG
-
 Email DLP, Integrated Cloud Email Security, Customer Stories
Email DLP, Integrated Cloud Email Security, Customer StoriesInsights on Human Layer Security from Tim Fitzgerald, CISO of Arm
-
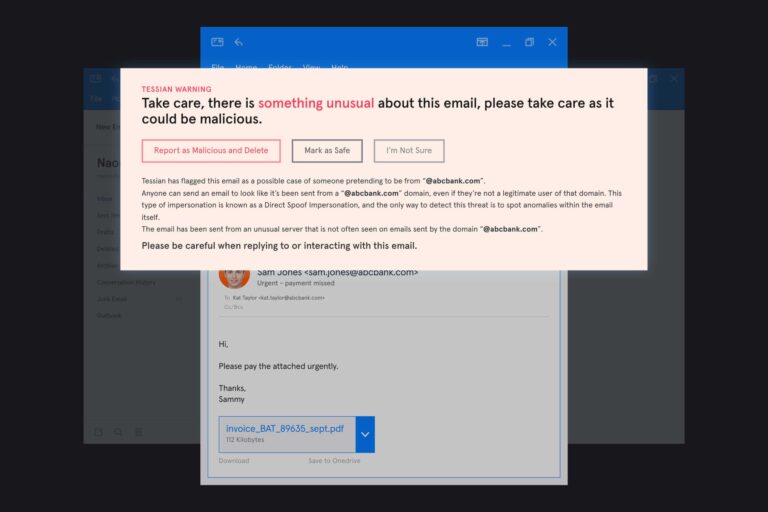 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Gisela Rossi From Tessian
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Niki Tailor From Tessian
-
 Email DLP
Email DLPHow a Gmail Design Flaw Causes Misdirected Emails
-
 Cyber Skills Gap
Cyber Skills GapOpportunity in Cybersecurity: Q&A With Amber Pham From TransUnion
-
 Email DLP
Email DLPA Brief History of Data Loss Prevention Solutions
-
 Email DLP, Integrated Cloud Email Security, Advanced Email Threats
Email DLP, Integrated Cloud Email Security, Advanced Email ThreatsA Year in Review: 2019 Product Updates
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityTessian Attends New Statesman’s Cybersecurity in Financial Services Conference
-
 Customer Stories
Customer StoriesEnsuring Data Security under GDPR
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsIt’s the Most Fraudulent Time of the Year
-
 Customer Stories
Customer StoriesSecuring Systems Amid Tight Regulation
-
 Advanced Email Threats
Advanced Email Threats7 Ways to Survive this Black Friday
-
 Customer Stories
Customer StoriesDefining Customer-First Culture with Email Security
-
 Interviews With CISOs
Interviews With CISOsTessian Spotlight: Bridget Kenyon, Global Chief Information Security Officer at Thales eSecurity
-
 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email SecurityThe Dark Side of Sending Work Emails “Home”
-
 Advanced Email Threats
Advanced Email ThreatsSpear Phishing Demystified: the Terms You Need to Know







