Integrated Cloud Email Security
- All Categories
- ...
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityFrom on-prem to cloud: Supporting your email security journey
-
 Life at Tessian, Integrated Cloud Email Security
Life at Tessian, Integrated Cloud Email SecurityTessian Named a Strong Performer in Enterprise Email Security by Independent Research Firm
-
 Integrated Cloud Email Security, Beyond the SEG / Microsoft + Tessian, Advanced Email Threats, Security Awareness Coaching
Integrated Cloud Email Security, Beyond the SEG / Microsoft + Tessian, Advanced Email Threats, Security Awareness CoachingLatest Microsoft Report Confirms Need for AI-Based Phishing Protection
-
 Integrated Cloud Email Security, Product Updates
Integrated Cloud Email Security, Product UpdatesRespond Faster. Prevent More.
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats
Integrated Cloud Email Security, Email DLP, Advanced Email ThreatsSecure Email Gateways (SEGs) vs. Integrated Cloud Email Security (ICES) Solutions
-
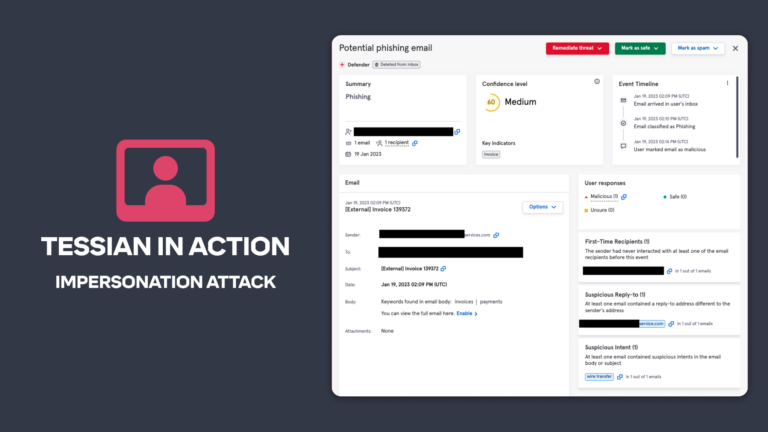 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsTessian in Action: Stopping an Impersonation Attack
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityWhat are Secure Email Gateways (SEGs) and Integrated Cloud Email Security (ICES) solutions – and how do they protect against email-based cybersecurity threats?
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email Threats1 in 5 Chief Information Security Officers (CISOs) Work More Than 25 Extra Hours Per Week
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityProduct Update: Advanced Malicious URL Protection
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityVideo: Tips For Cybersecurity Awareness Month
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsProduct Update: Enhanced Security Event Filtering and Reporting
-
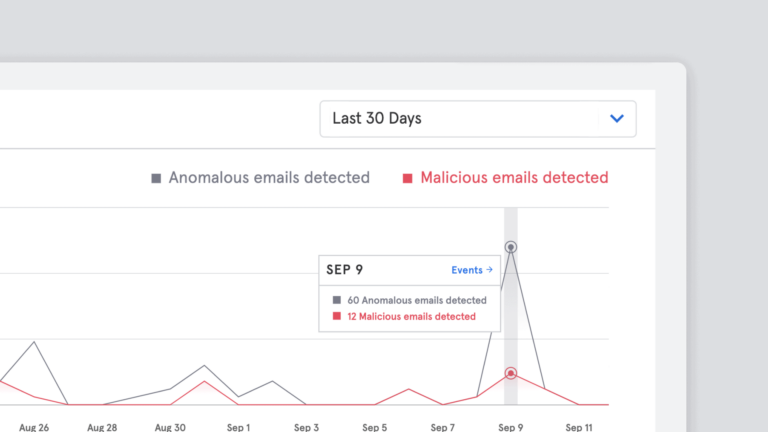 Integrated Cloud Email Security, Advanced Email Threats, Data & Trends
Integrated Cloud Email Security, Advanced Email Threats, Data & TrendsProduct Update: Improvement to Algorithms Sees 15% Increase in Detection of Advanced Email Threats
-
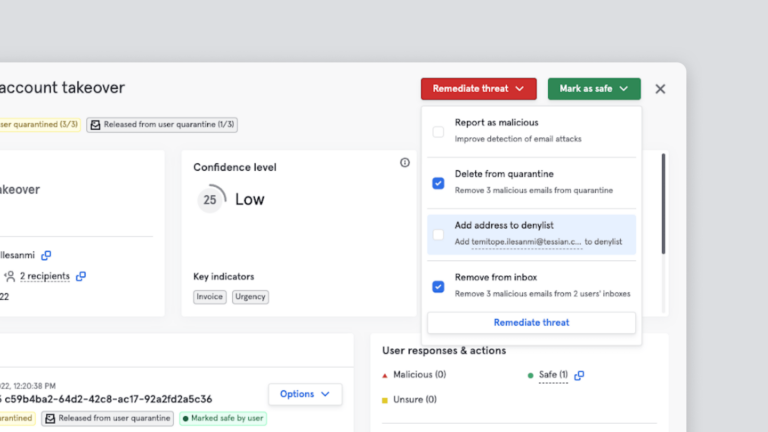 Integrated Cloud Email Security
Integrated Cloud Email SecurityProduct Update: Enhanced Event Triage to Speed Up Detection and Response to Malicious Emails
-
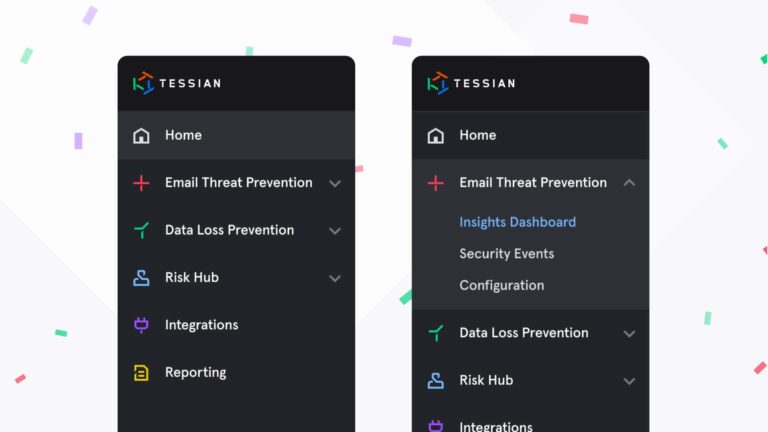 Integrated Cloud Email Security
Integrated Cloud Email SecurityProduct Update: Tessian Enhances Portal Navigation to Help Security Teams Respond to Incidents Faster
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityPhishing, Email Breaches and Multi-Factor Authentication Compromise Take Center Stage at Black Hat 2022
-
 Integrated Cloud Email Security, Interviews With CISOs
Integrated Cloud Email Security, Interviews With CISOsHot Takes: 8 Ways to Strengthen the CISO and CFO Relationship
-
 Integrated Cloud Email Security, Email DLP
Integrated Cloud Email Security, Email DLPTessian Recognized as a Representative Vendor in the 2022 GartnerⓇ Market Guide for Data Loss Prevention
-
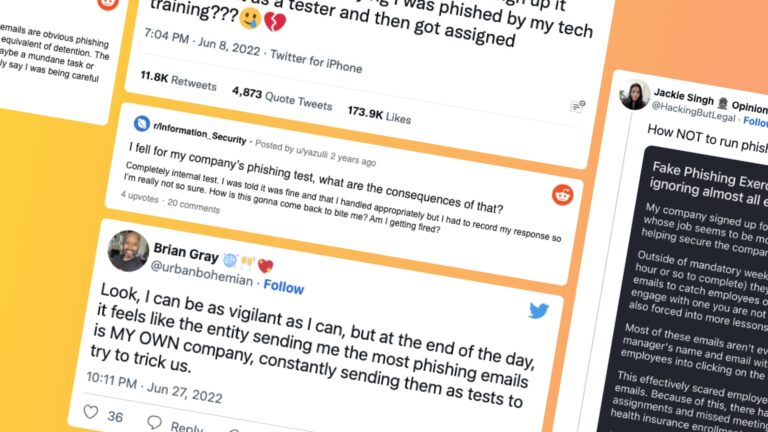 Integrated Cloud Email Security
Integrated Cloud Email SecurityHow to use phishing tests and in-the-moment cybersecurity awareness training to strengthen your cyber defenses
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsHow to Prepare for Increasing Cyber Risk
-
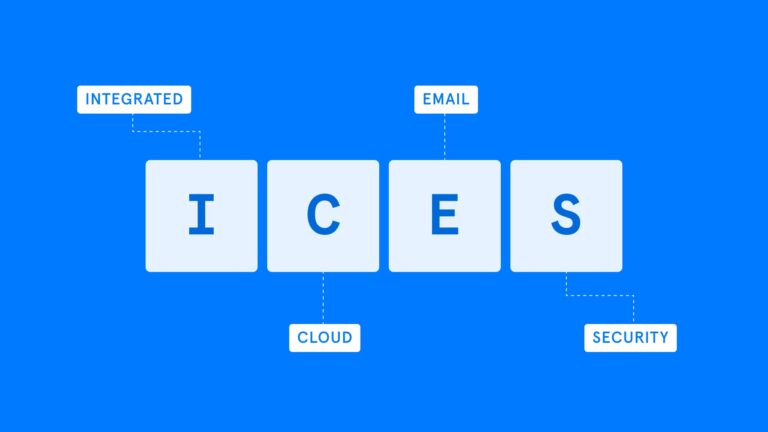 Email DLP, Integrated Cloud Email Security, Advanced Email Threats
Email DLP, Integrated Cloud Email Security, Advanced Email ThreatsWhat is an Integrated Cloud Email Security (ICES) Solution?







